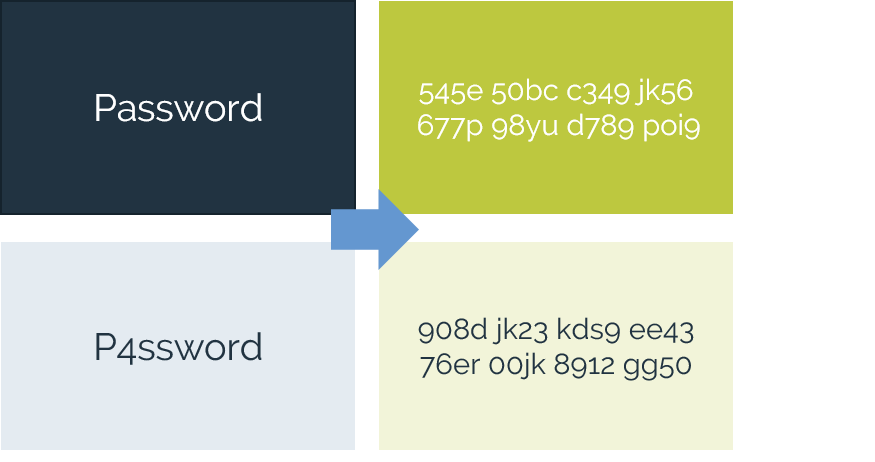
PRIVACY-ENABLED ANALYTICS
Maximize the value of your data while preserving privacy
Discovery and protection for your data analytics environment
Organizations are constantly looking for ways to utilize their data for business opportunities.
However, data privacy regulations require them to properly protect sensitive data of their clients, employees and partners.
The comforte Data Security Platform helps organizations to fully leverage the value of their data for analysis and innovation while preserving privacy and achieving compliance.
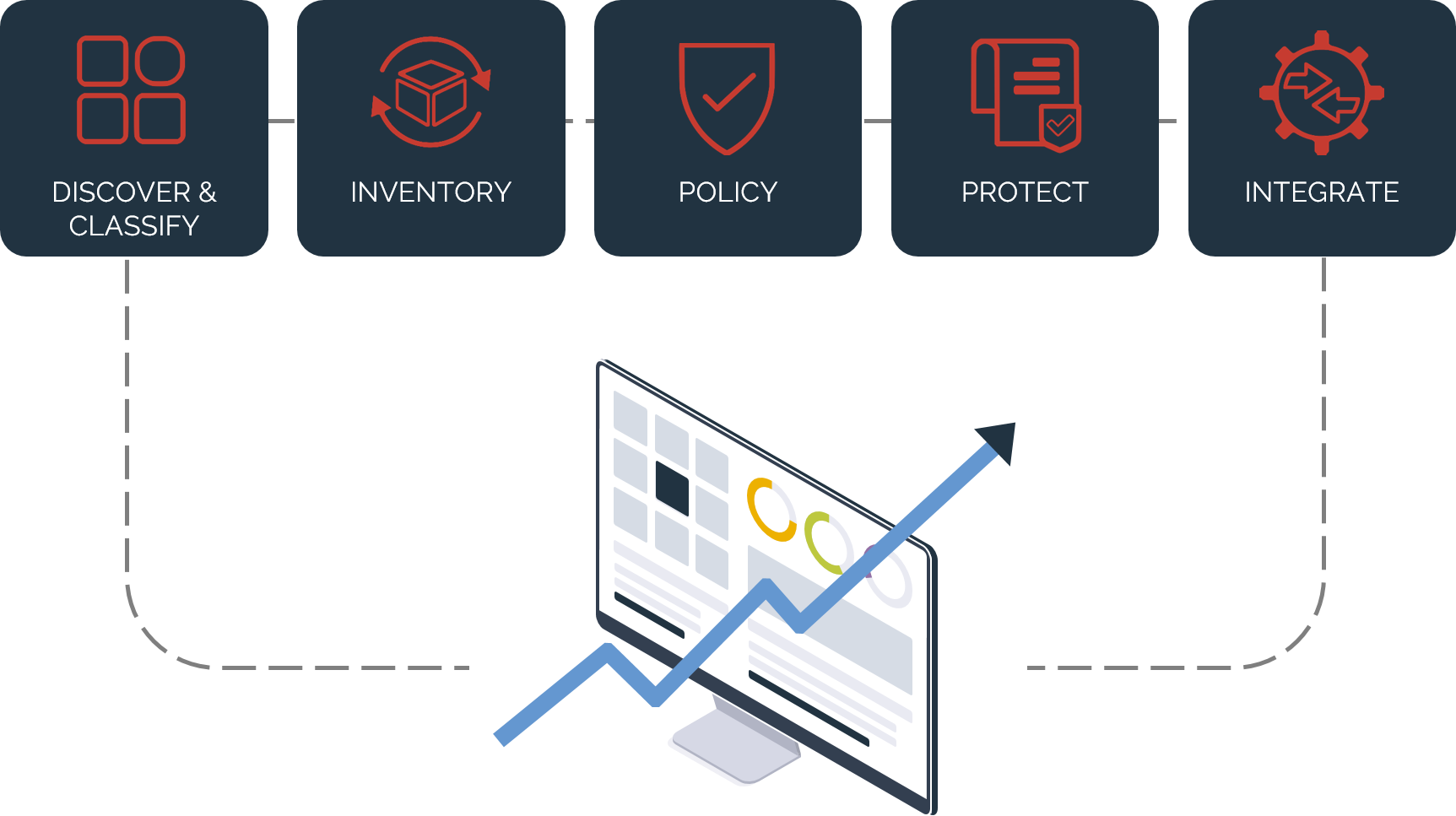
Key benefits
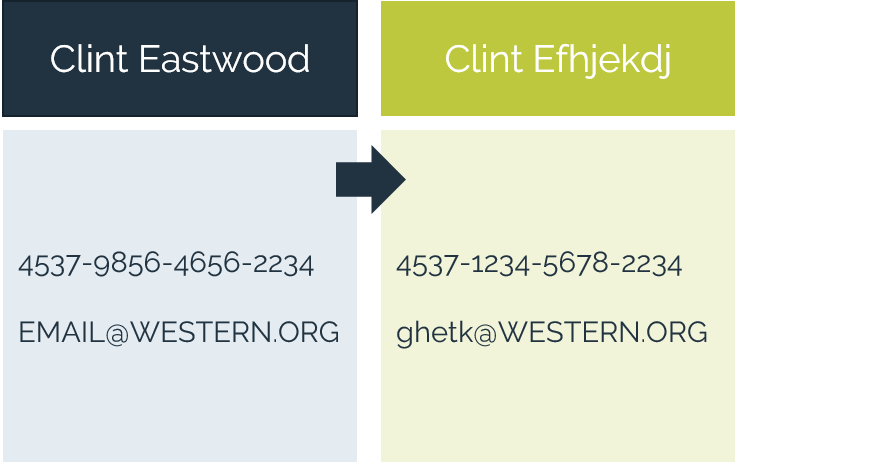
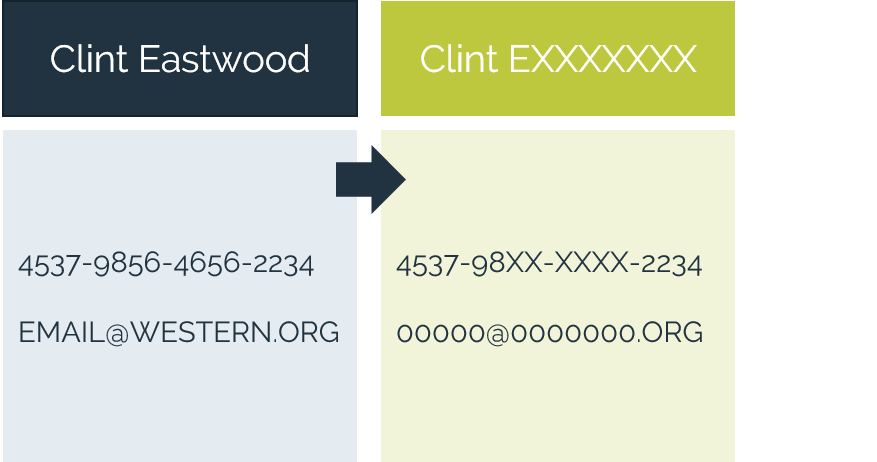
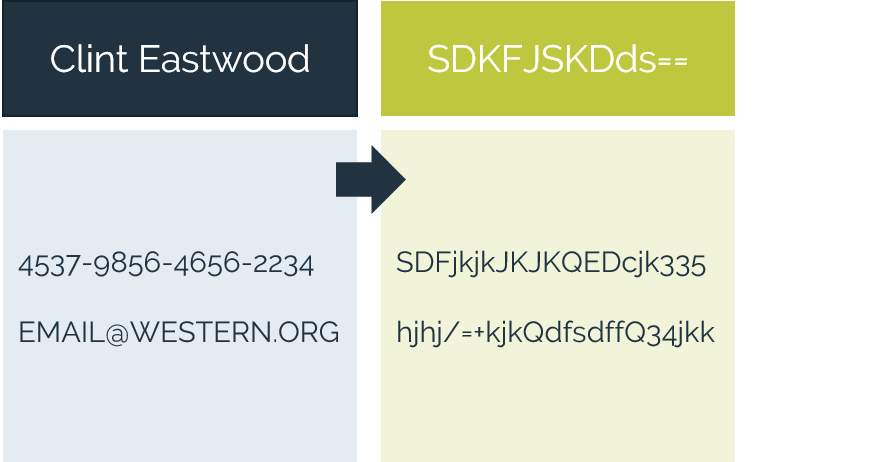
Leverage the business value of your data while preserving privacy with best-in-class discovery and protection solutions. Analyze protected data and utilize it for new business opportunities without security and compliance concerns.
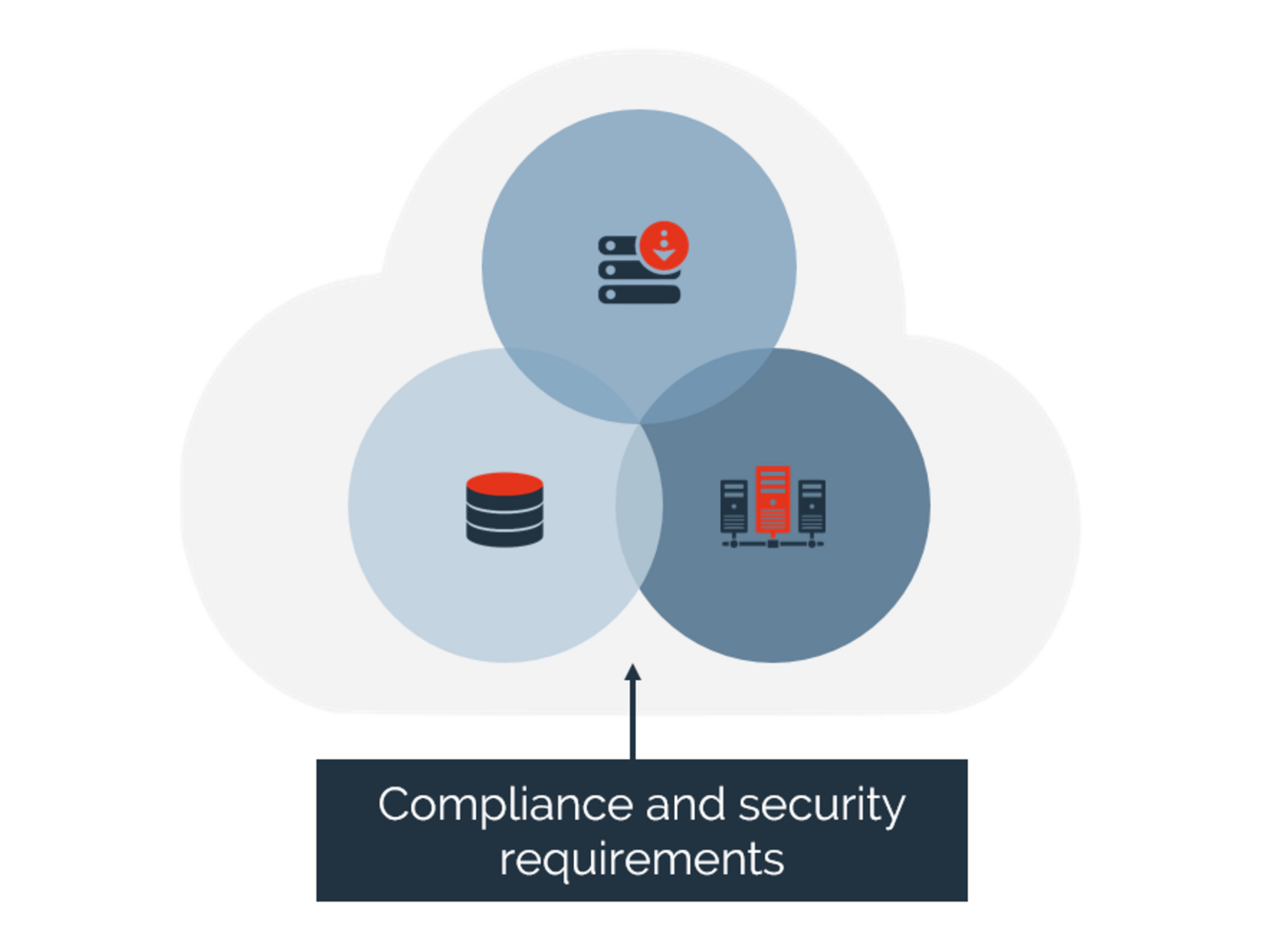
Ensure that appropriate policies and privacy preserving technologies are adopted to meet the compliance and security requirements for your data ecosystem. Protect data before it is ingested to your data warehouse (e.g. Snowflake) so that no sensitive information is stored in the cloud. Keep your data safe not only at-rest, but also in-motion or when it is in-use by analytics teams or shared with partners. Stay agile and easily adapt to existing and new regulations with future-proof data-centric security.
Reduce time to market for usable and actionable data. Implement privacy-preserving data protection in a matter of days or weeks, instead of months or years. Easily integrate with your data sources and stores, analytic tools and enterprise applications, whether they reside on-premises, in the cloud, or both.
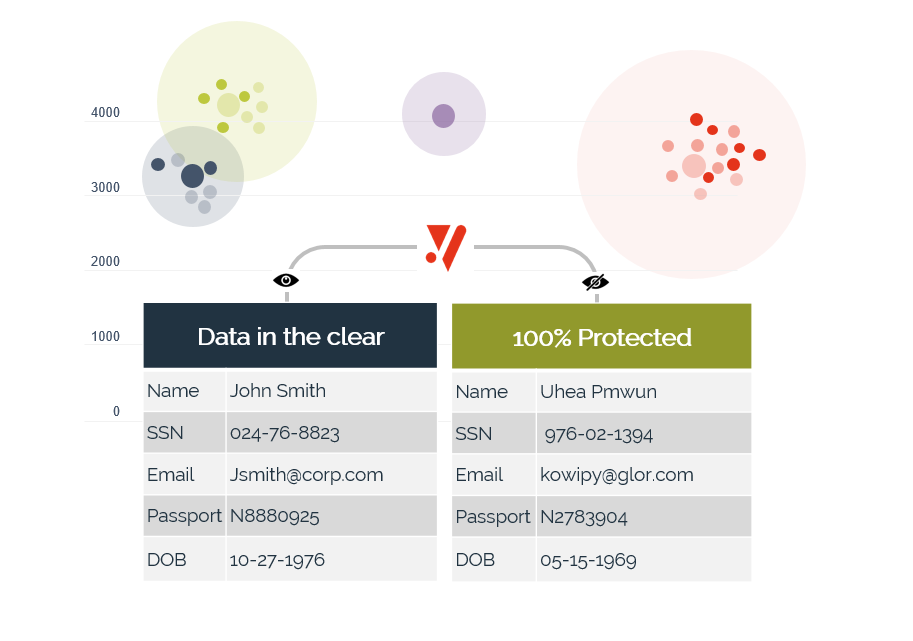
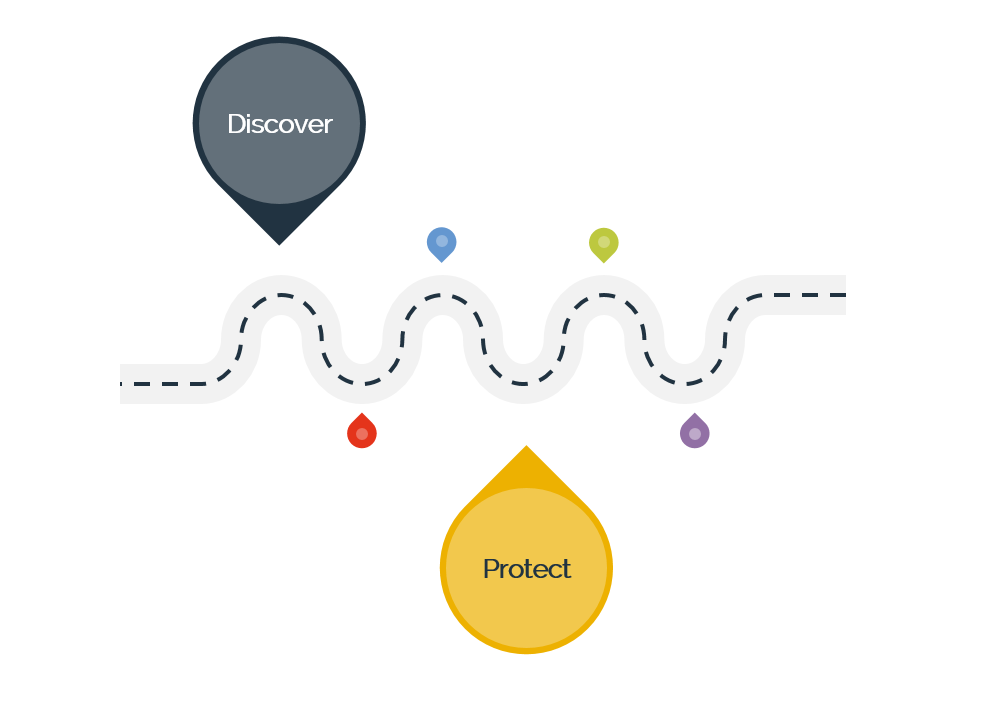
Discover and protect all of your sensitive data with an automated platform. Understand the data lineage so you can define your risk-based strategy faster and close data exposure gaps with appropriate data protection.
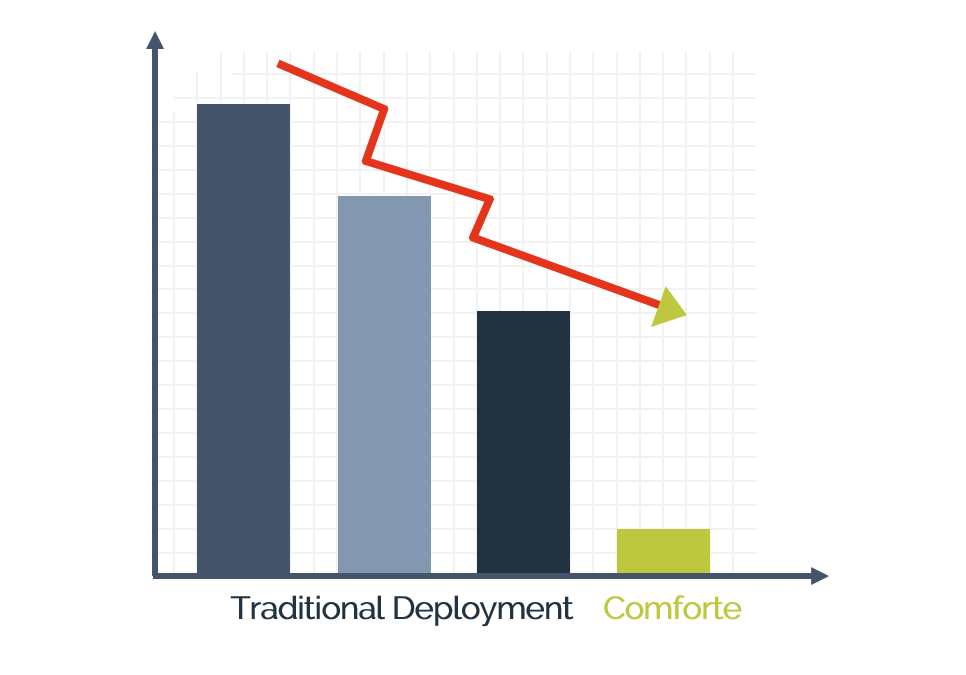
Once your data is protected, you will spend less resources for management and governance of sensitive data.
Demo: Secure data analytics
Watch
How it works
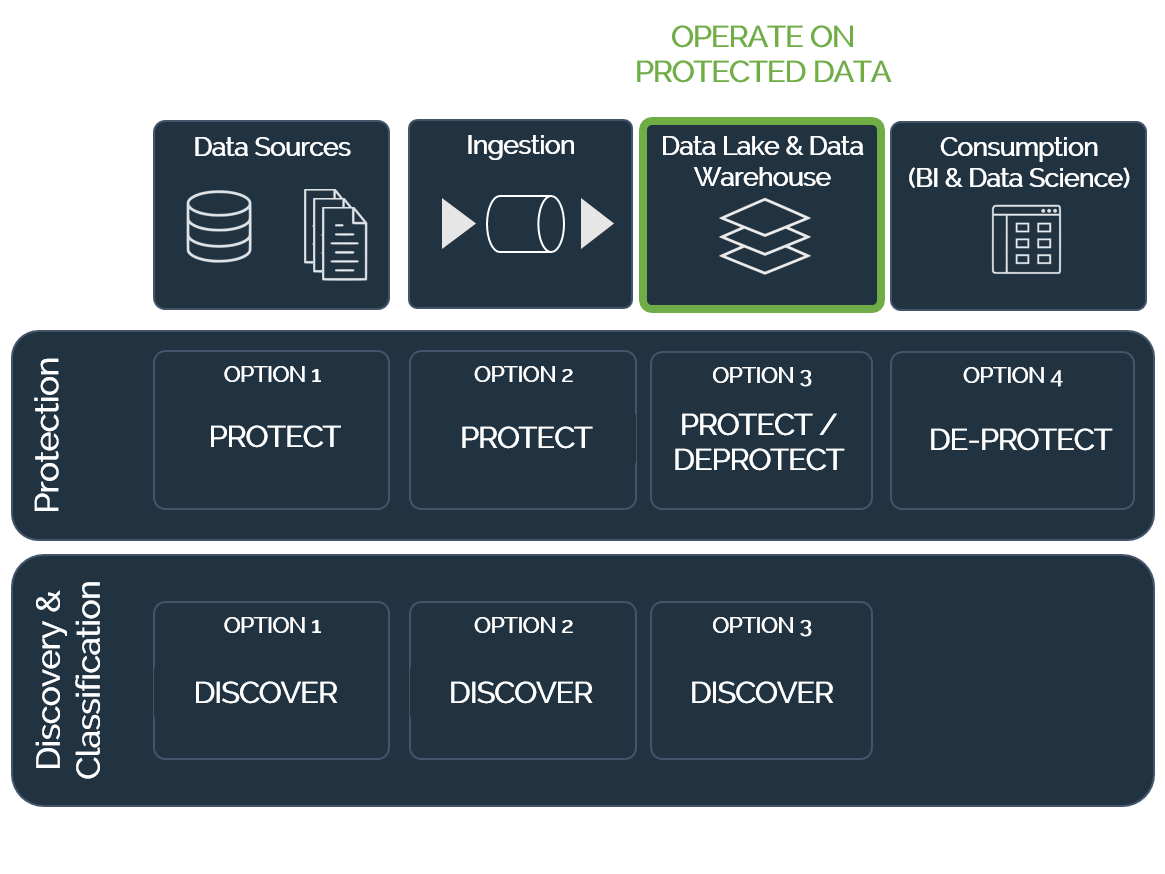
Architecture
- Locate any & all repositories containing structured, semi-structured, & unstructured sensitive data, even if you don’t know where it all is
- Protect data before it enters the cloud & in the cloud